Discord Minors Ransomware Complete guide will be discussed in this article.
The creators of Lunar virus are not alone: Online retailers offer a wide range of “grabber builders.”
When conducting research, unexpected things can occasionally come up. That was the experience that the Avast team had while looking into ransomware. They discovered what appeared to be typical ransomware, but they also noticed some strange features. First: A mere $25 was demanded as ransom.
Discord Minors Ransomware Everything You Want To Know
In this article, you can know about Discord Minors Ransomware here are the details below;
The researchers discovered after conducting additional research that this malware was renaming files with the suffix “.LUNAR” and encrypting them. They discovered more spyware in the family, but this time it was cryptocurrency miners and information thieves rather than ransomware.
This malware family wasn’t similar to the typical material the team saw, which left them perplexed. For what reason would someone spend time creating and disseminating something with such a slim chance of making money? Why is there such variation?
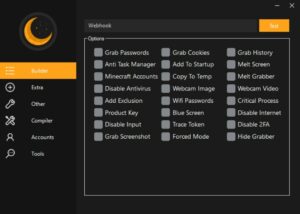
After more investigation, they discovered a Discord server devoted to the “Lunar” malware family, which they soon realized was a “malware-as-a-service” offering. A recent development that makes it possible to hack other individuals without any programming or technical knowledge is malware-as-a-service. Anyone interested in hacking can essentially just plug and play; all that’s needed is for users to decide which details, such a unique icon or binary to utilize as a carrier for the harmful code, need to be determined.
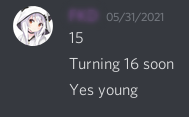
The malware’s developer was soliciting suggestions from customers, giving away freebies, and selling the infection on the Discord server. Community members would occasionally just hang out and chat or share plugins with one another. Furthermore, the Avast team discovered something unexpected when they observed the community’s behavior and terminology over time: the majority of its members were minors, mostly between the ages of 11 & 16.
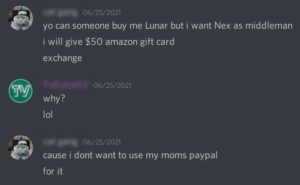
According to Jan Holman, a malware researcher at Avast, “we presume that this is precisely the explanation why the writer of Lunar, known on Discord as Nex, announces low expenses (5-25 EUR) for access to their malware builder.” This theory is further reinforced by the observation that the majority of community-submitted plugins and a large portion of the malware’s functionality are designed to annoy victims rather than actually harm them.
They also discovered that although the Lunar malware generator included features like ransomware, crypto mining, and password and information theft, those features weren’t their main marketing points. Instead, they concentrated on functions like taking over gaming accounts, erasing folders related to Minecraft or Fortnite, or continuously launching a web browser and accessing Pornhub.
Stated differently, pranks that could appeal to youngsters.
How does malware-as-a-service work?
The creators of Lunar virus are not alone: Online retailers offer a wide range of “grabber builders.” These are typically brief malware campaigns that are rebranded with a new name and logo, occasionally slightly altered or changed with additional functionality, and are based on source code from GitHub or even another builder.
They are all essentially the same, despite some differences in the functionality they supply, the functionality they offer, and the obfuscation utilized. Their names, logos, color schemes, and layouts are slightly different, but their.NET-based GUIs are similar. Nevertheless, their main feature remains the same: by clicking a few boxes and completing a few form fields, hackers may create unique malware samples.
Numerous builders, including Itr0ublveTSC, Mercurial, Snatch, HideGrabber, PirateStealer, AsteroidLLC, Stely, Viny, Rift, etc., are comparable to Lunar, according to the Avast team. These builders work in a similar way and share some code. There are comparable online forums and groups for the other builders as well.
Discord has blocked the servers linked to Avast’s research and stated that they take action against these kinds of communities.
Malware as community?
The community frequently offers assistance to the teenagers in figuring out how to install the malware-as-builder once they have it. They may use filenames and icons from authentic game executables to blend in with the background, or they could pose as cracked games or game hacks. Occasionally, they conceal the malicious code on a victim’s device by bundling it with legitimate, innocuous binaries.
Additionally, they use YouTube “bait” videos to entice victims and persuade them to download the needed content. The attacker sets up the video, uploads it to the Discord server, and everyone in the community comments on it, giving potential victims social validation. They even “warn” victims that their antivirus program might prevent the file from opening and provide instructions on how to set exceptions to allow the file to open.
Jan Holman, an Avast malware researcher, warns, “We strongly caution against downloading cracked software & game cheats, & especially against ignoring antivirus warnings & creating exceptions for such programs.” “It’s likely that a keygen or cracked game contains malware if your antivirus tool identifies it as such. The legality of your software is not the responsibility of the antivirus program.
However, despite the apparent support from the community, there is a lot of tension. The Avast team saw members stealing each other’s code and reselling it, as well as internal strife, instability, and possible bullying. These communities sometimes start off strong and fade away fast as the builders get disinterested or the negativity of the community gets to be too much for them. Also check Wifi4games Alternatives
This group has comparatively little effect in terms of real dangers. The Avast team didn’t intend to spend much time on it, but because the majority of the parties involved are kids, both the perpetrators and the victims, they decided to reveal their results.
Conversations like “I don’t want to use my mom’s PayPal,” “I don’t want to use her age,” and “taking over a teacher’s device during class” make that very evident. Discord informed Avast that in order to shield kids from unsolicited communications, parents should assist with customizing their settings. You may read more about parent safety on the Discord blog.
According to Holman, “kids may find these communities appealing because they think hacking is cool and malware makers offer a cheap and simple way to ‘hack’ someone and tell their friends about it.” They may also present an opportunity to pick up some programming skills; the community can be of some assistance there. But these actions are nonetheless against the law and should be mentioned.
Additionally, the Threat Labs team notes that these groups’ operational security was inadequate, with personal information being directly shared in chat rooms and social network accounts being readily accessible. Finally, even though the perpetrators’ acts can be seen as silly jokes, they could actually put their victims—and their victims’ parents, if they share devices—in risk by giving professional hackers access to their private information.
Researchers alerted Discord, who subsequently took the server offline, after Avast Threat Labs discovered and analyzed the server.