This post will explain Proxies For Email Protection. Today, organizations get an overflow of emails with harmful URLs or malware attachments. Cybersecurity companies provide email security services to secure sensitive communications and help corporations avoid Cyber attacks. By having the capability to examine emails from several IP addresses, high-quality proxies help in the detection of fraudulent content.
Ways To Use Proxies For Email Protection?
In this article, you can know about Ways To Use Proxies For Email Protection? here are the details below;
Companies that provide services to safeguard emails from being intercepted or edited need to move quickly to keep their operations efficient and successful. In such cases, there is a risk that their consumers would complain about being inconvenienced. To defend against cyber attacks, cybersecurity organizations must choose email protection solutions that do not expose them to any potential dangers.
What is an Email Proxy?
A mail proxy server is an independent computer placed before the email server. The mail proxy server is configured to deliver any or all of the services, including Web based email through IMAP, Virus detection, File type blocking, File size blocking, and Spam filtering. Proxies for Email protection may helps in growth of your business.
Are Proxy Servers Safe?
Paid proxy services are generally safe to use. They give the user safe anonymity and are often quick, dependable, and transparent. Of course, check the evaluations of a proxy before using it; nonetheless, most commercial proxy programs are verified and can be trusted for Email Protection.
What is Proxy Server?
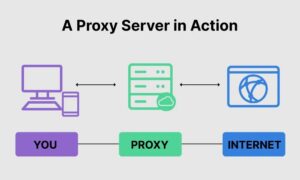
As a proxy, or proxy server, it acts as a conduit for all your internet traffic, acting as an intermediary between your computer and the internet. Your computer’s inquiries are directed through the proxy to a new IP address, assuring the complete privacy of your web browsing. Using proxies may go a long way toward protecting your identity in a world where identity theft is prevalent on the internet. Whether you operate a large or small email-based business, employing proxies for email protection is essential nowadays.
How to Use Proxies For Email Protection?
Businesses that provide Proxies for Email protection prevent threats from reaching their intended recipients. They thoroughly examine every outgoing and receiving email to detect any fraudulent attempts. This activity is carried out by cybersecurity businesses using customized scrapers. These scrapers check suspicious links to see whether they lead to good sites. When suspected attachments are received, a similar procedure happens. All files are opened in a virtual computer to monitor all activity, especially those interacting with external services. To retain a concealed and engaging presence, cybersecurity businesses must act swiftly.
If, on the other hand, all connections come from the same IP address, hackers or cyber criminals will rapidly figure out that cybersecurity groups are verifying emails and files. They would be able to design counter-strategies for cybersecurity corporations.
Skilled hackers create specific phishing URLs and viruses that disguise all suspicions at first sight. For example, counterfeit content may look secure and reputable when accessed via a particular range of IP addresses. Furthermore, hackers may create fake websites that look trustworthy and safe when victims access them from specified geo-locations.
Email protection is useless without proxies since cybersecurity firms cannot identify phishing and viruses. It is why Proxies For Email Protection are so essential.
Email Protection with Proxy Services
Every firm receives many emails with harmful URLs or malware attachments. Therefore, they use email security systems that scan all incoming messages. In addition, proxies inspect each email for harmful links and attachments before its delivery.
1. The secret to safe communication
Encryption ensures data confidentiality and legal security. PGP and S/MIME-based encryption secure the safety of your email correspondence. It is a simple, straightforward encryption solution that complies with the General Data Protection Regulation (GDPR).
2. Securely transmit emails and documents
It provide a straightforward method for securely transmitting emails and documents without using cryptographic keys. It transforms the email and any attachments into a password-protected PDF file. The recipient is instantly supplied the password through text message.
Centralized management of email signatures and cryptographic keys enables you to communicate with your partners securely and conveniently. The gateway, and not the client, manages all certificates and cryptographic keys.
Types of Proxies For Email Protection
There is a vast selection of proxies available. Here are a few examples.
1. Residential Proxies
Residential proxies are proxies whose IP addresses are residential. Consider, for instance, a person with an active Internet connection at home. The Internet Service Provider has issued the homeowner a household IP address (ISP). If the homeowner sells their residential IP address to a non-resident, the residential IP address becomes a residential proxy. Residential Proxies for Email protection provide high anonymity because they are actual and connected with a specific location, connection, and ISP.
2. Data Center Proxies
It is the most used sort of proxy. In contrast to residential proxies, which have an actual IP address, data center proxies have a fake IP address. In comparison to residential proxies, data center proxies are more likely to be banned, even though they are notably faster. Always insist on purchasing data center proxies from a reputable source.
All proxy kinds may be either semi-dedicated, shared, or private. Private or dedicated proxies are those used by a single end user. For example, if you acquire a private proxy, you are the only one with access to and control over it. It is the most acceptable proxy type for any company.
Shared proxies are the sort of proxies used by several users – to create anonymity; multiple clients use the same proxy simultaneously. Shared proxies are less expensive than dedicated proxies since the users that use the proxy also share the proxy’s cost.
You must choose which sort of Proxies for Email Protection is ideal for your company.
Why Should You Use Proxies For Email Protection?
Proxy servers are essential since they assist examine all outgoing and incoming emails for fraudulent activity. The whole email protection system may be down if proxies do not function. Proxy servers are an essential tool in cyber security for preserving your online privacy. Proxy servers work as intermediaries between your computer and the websites you browse. Proxies for Email Protection make it difficult for hackers and cybercriminals to check your emails.
- Phishing Email Protection
- Prevention of Distributed Denial of Service attacks (DDoS)
- Protecting Your Brand/Impression
- Protection Against Attacks and Data Breach
- Malware Prevention
How To Check Your Email Using A Proxy Server
Proxies for Email Protection are crucial to the success of any online business. Using a proxy server to check your email in a country with Internet restrictions is an anonymous method of accessing your inbox. Following are the steps required to check the mailbox. This method makes the task simpler and safer.
1. Purchase Proxies
To check your email, a valid proxy subscription is required. You should use paid Proxies for Email Protection. It is because free proxies should not be used to check your email since your email may be hacked.
2. Configure Browser Proxies
Configuring proxies depends on the browser you want to use since the instructions vary somewhat. However, the steps for configuring proxies in Internet Explorer, Chrome, and Firefox are shown here.
- Internet Explorer
Users of Internet Explorer should click Tools in the menu bar, then Internet, then the connections Tab, and then pick LAN settings. Make sure the Box next to LAN is ticked. You then continue to enter the IP address and port numbers provided by the selected Proxy. Proceed by clicking the “OK” button.
- Chrome
If you are using Google Chrome, select the Menu button, which is always located in the upper-right corner, and click settings. Enter ‘Proxy’ in the box to do a fast search. Select Proxy from the results list to see the Internet Properties dialogue box.
From there, go to ‘LAN SETTINGS,’ then check the box next to ‘use proxy a proxy server for your LAN,’ and then enter the proxy’s IP address and port number. Finally, save this configuration by clicking “OK.”
- Firefox
For those using the Firefox web browser, click the Firefox button at the top of the window to modify your proxy settings. Next, move the pointer to the submenu and choose ‘options,’ then select the ‘Network tab’ and settings. Finally, select the Manual option for proxy setup settings. The proxy server’s IP address and port number may be entered here. Finally, click “OK” to save the current setup.
3. Login with the Proxy Server
After your borrower has been set to use the proxy, you may access your email by signing in. For proxies with URL input interfaces, just visit the proxy’s homepage and enter the web address of your email provider. For instance, enter www.gmail.com in the area given. It will load the official website, where you may enter your credentials to log in.
FAQs
Q. What Are Proxies for Email Protection?
Proxies for email protection are proxy servers that you may use to conceal your IP address while checking your email or using anti-malware software to safeguard your email. Notably, there are no proxy servers specially designed for this purpose.
Because there is no unique need, standard proxy services may be used to do this. However, the proxies you use must be safe, confidential, dependable, and quick enough to do the task without causing frustration.
Q. Why Use Proxies for Checking Emails?
There is no question that companies get many emails containing dangerous threats. Some of these malicious programs aim to steal your IP address. If you fall for the hack without using a proxy server or a proxy-like system, your IP address will be known and used for anything they require.
Proxies For Email Protection software are designed to monitor emails for harmful actors; these applications need proxies to conceal their operations from hackers.
Q. Is it Safe to Use Proxies for Email Checking?
Using proxies to check your email is designed to be secure. However, this is only true for proxy services that are safe and trustworthy. If a proxy service does not monitor your traffic and is fast enough to prevent hacking and eavesdropping, it may be used to check your email. Therefore, proxy servers are often used to examine and safeguard email.
Final Words For Proxies For Email Protection
Proxies for Email protection might seem difficult at first sight. They differ in efficiency, security, and reliability depending on the type you decide on employing and whether or not it matches your objectives. However, regarding emails, four things should be included in whichever form of proxy you use, i.e., Encryption, Monitoring, Privacy, and IP address reliability.
Scams and fraud on the internet may be reduced using proxy servers. For cybersecurity efforts, you may make use of many proxies. On the other hand, the data center proxies are preferred owing to their lightning-fast speed, uptime, and unsurpassed performance. In addition, you may use reverse proxies and transparent proxies to defend against DDoS and malware attacks on your servers and network, respectively.