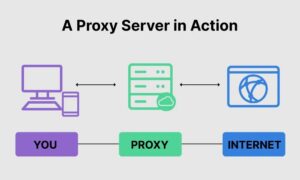
A proxy server is an app that works as an interface between a client requesting a service and the server providing that resource in computer networking. For example, instead of connecting directly to a server that can fulfill a request for help, such as a file or a web page, the client refers the request through the proxy server, which assesses the request and conducts the necessary network transactions. This approach helps simplify or regulate the request’s complexity or gives extra advantages such as load balancing, privacy, or security. To bring structure and encapsulation to distributed systems, proxies were created. Thus, a proxy server works on behalf of the client while requesting service, possibly concealing the request’s actual origin from the resource server.
Guide About Proxy Server? How To Use It ?
In this article, you can know about Guide About Proxy Server? How To Use It ? here are the details below;
What is Proxy Server?
A proxy server is a device or router that provides a connection point between users and the internet. As a result, it helps in preventing cyber hackers from accessing a private network. In addition, it is a server that acts as an “intermediary” between end-users and the websites they browse online. An IP address is employed when a computer or device connects to the internet. It is comparable to your home’s street address in that it controls incoming data and provides a return address for other devices to verify. A proxy server is a machine on the internet with its IP address.
Network Security and Proxy Servers
Proxies provide an extra layer of protection to your computer. For example, they may be configured as web filters or firewalls, shielding your computer from online risks such as viruses. This added protection is also helpful with a secure web gateway or email security tools. For example, it allows you to filter traffic based on its degree of safety or the amount of traffic your network—or individual computers—can manage.
How should a proxy be used?
Some individuals use proxies for personal reasons, such as concealing their location when viewing movies online. However, for a business, they may be used to achieve various vital functions such as:
- Improve security
- Protect your workers’ online activities from prying eyes.
- To avoid crashes, balance internet traffic.
- Control the websites that workers and office personnel have access to.
- Reduce bandwidth consumption by caching files or compressing incoming data.
How a Proxy Works
A proxy server functions as a go-between for a computer and the internet since it has its IP address. When you submit an internet request, it is routed to the proxy, which receives the answer from the web server and sends the data from the webpage to your computer’s browser, such as Chrome, Safari, Firefox, or Microsoft Edge.
How to Get a Proxy
Versions of hardware and software exist. Hardware connections link your network to the internet, where they receive, transmit, and forward data from the internet. Typically, software proxies are hosted by a provider or live in the cloud. You download and install a program on your computer that allows you to communicate with the proxy. A software proxy is often available for a monthly subscription. They are sometimes free. Free proxies often provide fewer addresses and may only cover a few devices, while commercial proxies may fulfill the needs of a corporation with numerous devices. Also check proxies for email protection
How Is the Server Configured?
To begin using a proxy server, you must first setup it up on your computer, device, or network. Each operating system has its setup processes, so follow your computer or network requirements. However, in most circumstances, setup entails employing an automated configuration script. If you wish to do it manually, you may input the IP address and the suitable port.
How Does the Proxy Protect Computer Data and Privacy?
A proxy server serves as both a firewall and a filter. An end-user or a network administrator may select a proxy to safeguard data and privacy. It checks the data that enters and exits your computer or network. It then applies restrictions to prevent you from exposing your digital address to the rest of the world. Hackers or other undesirable actors only view the proxy’s IP address. People on the internet cannot access your data, schedules, applications, or files without your specific IP address. With it in place, web requests are sent to the proxy, which then connects to the internet and retrieves the information you want. Passwords and other personal data are protected further if the server supports encryption.
Advantages of Using a Proxy Server
Proxies have various advantages that might help your business:
Improved security: This can function as a firewall between your computers and the internet. Without them, hackers may quickly get your IP address and exploit it to attack your computer or network. Private browsing, viewing, listening, and shopping: Use proxies to avoid being bombarded with unwanted advertisements or collecting IP-specific data.
Access to location-specific content: You may configure a proxy server with an IP address from another country. You may be in that nation and receive complete access to all of the stuff computers in that country are permitted to interact with. Stop workers from visiting improper or distracting websites: You may use it to restrict access to websites that violate your organization’s ideals. You may also ban websites that are known to distract staff from critical activities. For example, several companies restrict social networking sites such as Facebook and others to eliminate time-wasting temptations.
Types of Proxy Servers
While all proxy servers provide users with an alternative internet address, there are various distinct types, each with its unique set of functions.
1. Forward Proxy
A forward proxy is a server that stands in front of clients and routes data to groups of users inside an internal network. When a request is submitted, the proxy server analyses it to determine whether or not to make a connection.
A forward proxy best works for internal networks needing a centralized access point. It secures IP addresses for people on the network and enables simple administrative administration. A forward proxy, on the other hand, may hinder an organization’s capacity to cater to the demands of particular end-users.
2. Transparent Proxy
A transparent proxy may provide users with an experience similar to that of their home computer. It is “transparent” in this sense. However, they may also be “forced” on users, which means they are linked without knowledge.
Transparent proxies are ideal for businesses that wish to use a proxy without making workers aware of it. It has the benefit of offering a consistent user experience. On another side, transparent proxies are more vulnerable to security risks, such as SYN-flood denial-of-service attacks.
3. Anonymous Proxy Server
An anonymous proxy is designed to make online activity untraceable. It operates by accessing the internet on the user’s behalf while concealing their identity and computer information.
A transparent proxy is ideal for individuals who seek complete privacy while browsing the internet. While transparent proxies provide some of the most excellent identity protection, they have certain limitations. Many people see transparent proxies as unethical, and users may encounter opposition or prejudice.
4. High Anonymity Proxy
It is an anonymous proxy that goes above and beyond anonymity. It works by deleting your data before the proxy tries to connect to the destination site.
The server is best for users who want complete anonymity, such as workers who do not want their behavior traced back to the firm. On the other hand, some of them, especially the free ones, are decoys that trick users into revealing personal information or data.
5. Distorting Proxy
A distorting proxy presents itself as a proxy to a website while concealing its true identity. It is accomplished by changing its IP address to an erroneous one.
People who wish to mask their location when using the internet should use distorting proxies. This form of proxy may make it seem as though you are surfing from a specific nation and gives you the benefit of concealing not only your identity but also the identity of the proxy. In addition, it implies that your identity is safe even if you are connected to the proxy. However, some websites immediately ban distorting proxies, preventing end users from accessing sites they need. Also check proxies for email protection
6. Data Center Proxy
Datacenter proxies are not offered by an internet service provider (ISP) but rather by another organization through a data center. This proxy server is located in a physical data center, and user requests are routed.
Datacenter proxies are an excellent option for those that want rapid response times and a low-cost solution. As a result, they are an excellent alternative for anyone who needs to acquire information about a person or organization rapidly. They have the advantage of allowing users to capture data quickly and cheaply. On the other hand, they do not provide maximum anonymity, which may expose users’ personal information or identity.
7. Residential Proxy
A home proxy provides an IP address associated with a particular physical device. All subsequent queries are routed through that device.
Residential proxies are ideal for customers who need to validate the advertisements that appear on their website to prevent cookies and suspicious or unwelcome advertisements from rivals or unscrupulous actors. Residential proxies are more reliable than other types of proxies. However, they often cost more, so consumers should consider whether the advantages outweigh the added expense.
8. Public Proxy
A public proxy is available to everyone for free. It operates by granting users access to its IP address, which allows them to remain anonymous when visiting websites. Public proxies are best suited for users that choose money above security and speed. Although they are free and free, they are often sluggish due to many free users. In addition, when you use a public proxy, you face the danger of your information being accessed by others on the internet.
Several users use shared proxies at the same time. They provide you with an IP address that may be shared by other people, allowing you to surf the internet while pretending to be at a place of your choosing. Shared proxies are an excellent choice for folks who have little money to spend and do not need a fast connection. The primary benefit of a shared proxy is its cheap cost. However, because others share them, you may be blamed for someone else’s poor actions, resulting in your site being blocked.
10. SSL Proxy
Decryption is provided through a secure sockets layer (SSL) proxy between the client and the server. The proxy conceals its presence from both the client and the server since the data is encrypted in both ways.
These proxies are ideal for enterprises that want increased security against attacks that the SSL protocol detects and prevents. In addition, because Google likes SSL-enabled servers, using an SSL proxy with a website may improve its search engine position. On the negative, since material encrypted on an SSL proxy cannot be cached, you may notice poorer performance while accessing websites several times.
11. Rotating Proxy
Each user that connects to a rotating proxy is assigned a unique IP address. Users are given an address distinct from the device that connected before them. Users that need to perform a lot of high-volume, continuous web scraping will benefit from rotating proxies. They let you return to the same website anonymously again and over. However, it would help if you exercised caution while choosing rotating proxy services. Some use public or shared proxies, which may expose your data.
12. Reverse Proxy
In contrast to a forward proxy, placed in front of clients, a reverse proxy is placed in front of web servers and is responsible for directing browser requests to the appropriate web server. The operation is carried out by intercepting user requests at the network edge of the web server. After that, it communicates with the origin server to get replies by sending requests.
Popular websites that manage the load of many incoming requests might benefit significantly from using reverse proxies.
They may function as an additional web server for an organization, managing incoming requests, which can help an organization cut down on its need for bandwidth. The disadvantage is that reverse proxies may disclose the HTTP server architecture if an attacker can overcome them. In addition, network administrators may need to beef up or reconfigure their firewall if a reverse proxy is used.
VPN vs. Proxy Server
Virtual private networks (VPNs) and Proxy servers may seem alike on the surface since they both route requests and answers through an external server. Both also let you access websites otherwise blocked in the nation where you are physically situated. VPNs, on the other hand, provide superior security against hackers since they encrypt all communication.
Choosing VPN or Proxy
If you want to use the internet to continually transmit and receive encrypted data, or if your firm needs to divulge data you need to conceal from hackers and corporate spies, a VPN is a better option.
A proxy server may suffice if an organization only wishes to enable its users to access the internet anonymously. It is preferable if you merely want to know which websites your team members are visiting or if you want to ensure they have access to websites that restrict users from your country.
Because users often want secure data transfer in both ways, a VPN is more suited for corporate usage. In the wrong hands, company information and employee data may be pretty valuable, and a VPN offers the encryption required to keep it safe. On the other hand, a proxy server may be an appropriate alternative for personal usage if a breach would only harm you, a single user. You may also employ both technologies simultaneously, which is helpful if you want to restrict the websites that users on your network access while still encrypting their conversations.
FAQs
1. What is a proxy server?
A proxy server is a device or router that acts as a connection point between users and the internet. As a result, it aids in preventing cyber intruders from infiltrating a private network.
2. How does a proxy server function?
A proxy server functions as a go-between for a computer and the internet since it has its IP address. When you submit an internet request, it is routed to the proxy, which receives the answer from the web server and sends the data from the web page to your computer’s browser, such as Chrome, Safari, Firefox, or Microsoft Edge.
3. VPN vs. proxy server?
Virtual private networks (VPNs) and Proxy servers may seem alike on the surface since they both route requests and answers through an external server. Both also let you access websites otherwise blocked in the nation where you are physically situated. VPNs, on the other hand, provide superior security against hackers since they encrypt all communication.
4. What are the Advantages of using a proxy server?
A proxy server provides better security, private browsing, viewing, and listening, access to location-specific material, and prevents employees from visiting undesirable or distracting websites.